Empower Your Security: The Ultimate Guide to Security Risk Assessment

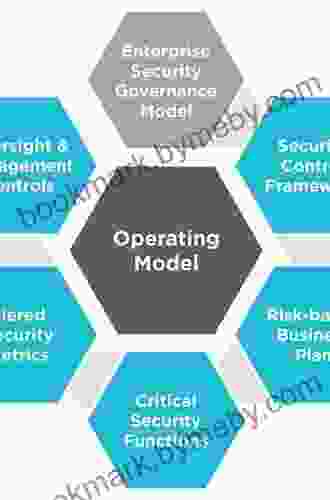
In today's rapidly evolving threat landscape, protecting your organization from security risks is paramount. A comprehensive security risk assessment is the foundation of an effective security program, empowering you to identify, prioritize, and mitigate potential threats to your physical and operational assets. 4.2 out of 5 This comprehensive guide delves into the essential aspects of security risk assessment, providing you with the knowledge and tools to safeguard your organization from harm. A security risk assessment is a systematic process of identifying, analyzing, and evaluating potential security risks to an organization's assets. It encompasses both physical security, such as the security of buildings, equipment, and materials, and operational security, which addresses vulnerabilities in processes, procedures, and information systems. By conducting a thorough risk assessment, you can gain a clear understanding of the threats your organization faces, their potential impact, and the appropriate measures to mitigate them. A comprehensive security risk assessment offers numerous benefits for your organization, including: The process of conducting a security risk assessment typically involves the following steps: Numerous tools are available to assist you in conducting security risk assessments. These tools can streamline the process, enhance accuracy, and provide valuable insights: A comprehensive security risk assessment is an indispensable tool for safeguarding your organization from a myriad of threats. By adopting a systematic approach to risk management, you can proactively identify, prioritize, and mitigate potential risks, ensuring the security of your physical and operational assets. Empower your security today by downloading our comprehensive guide to security risk assessment. Equip yourself with the knowledge and tools to protect your organization from the evolving threat landscape.Language : English File size : 2597 KB Text-to-Speech : Enabled Screen Reader : Supported Enhanced typesetting : Enabled Word Wise : Enabled Print length : 213 pages What is a Security Risk Assessment?
Why is Security Risk Assessment Important?
Conducting a Security Risk Assessment
Tools for Security Risk Assessment
Download Your Copy: Security Risk Assessment: Managing Physical and Operational Security
4.2 out of 5
| Language | : | English |
| File size | : | 2597 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 213 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Kathleen Buckstaff
Kathleen Buckstaff Jonathan A Knee
Jonathan A Knee Michael Powell
Michael Powell Jackie Morris
Jackie Morris Sam J Miller
Sam J Miller Jacqueline Mcassey
Jacqueline Mcassey Isidra Mencos
Isidra Mencos William Beckford
William Beckford Jay Wengrow
Jay Wengrow Jack Cole
Jack Cole Jackie Glenn
Jackie Glenn William J Poorvu
William J Poorvu Lisa Ferrel
Lisa Ferrel Jack Hunnicutt
Jack Hunnicutt J Dominique
J Dominique Isabella Morris
Isabella Morris J Andrew Royle
J Andrew Royle James Burnes
James Burnes Iris Apfel
Iris Apfel J Mark Souther
J Mark Souther
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Hunter MitchellRestitution: Space Colony One – A Thrilling Journey of Hope and Survival on a...
Hunter MitchellRestitution: Space Colony One – A Thrilling Journey of Hope and Survival on a... Yasushi InoueFollow ·15k
Yasushi InoueFollow ·15k Preston SimmonsFollow ·12k
Preston SimmonsFollow ·12k Jean BlairFollow ·15.3k
Jean BlairFollow ·15.3k Rodney ParkerFollow ·18.8k
Rodney ParkerFollow ·18.8k Robert Louis StevensonFollow ·3.6k
Robert Louis StevensonFollow ·3.6k Efrain PowellFollow ·3.6k
Efrain PowellFollow ·3.6k Jerry HayesFollow ·8k
Jerry HayesFollow ·8k Ralph Waldo EmersonFollow ·18.3k
Ralph Waldo EmersonFollow ·18.3k

 Phil Foster
Phil FosterThe Unforgettable Easter: Ramona's Journey of Discovery...
Embark on Ramona's Extraordinary Easter...

 Levi Powell
Levi PowellThe Old City and Mount of Olives: A Journey Through...
Jerusalem, a city etched into the annals of...

 Henry Hayes
Henry HayesThe Clearances: A Journey Through Scotland's Hidden...
In the 18th and 19th...

 Edward Reed
Edward ReedUnravel the Enigmatic 'Path of Bones' with Cassie Quinn...
Step into the...
4.2 out of 5
| Language | : | English |
| File size | : | 2597 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 213 pages |